Creating a Custom Rule
Criteria, Actions, and Applying Custom Rules
Unlike Allow and Block Rules, Custom Rules can be multi-conditional, based on the following criteria:
Sender address, or domain
IP address or range
Subject
URLs
Headers
Attachment types
Custom Rules actions are as follows:
Deliver
Deliver + Banner (Only available Mesh Unified and Mesh 365)
Deleted
Quarantine
Rejected
Junk (Only available Mesh Unified and Mesh 365)
Junk + Banner (Only available Mesh Unified and Mesh 365)
Custom Rules Can Be Applied:
Globally - Can be created from the partner level for all or selected customers.
Organizationally - Can be created for a specific customer.
Domain - Can be created for a specific domain.
Users - Can be created for specific users or mailboxes.
What Do Custom Rules Bypass if Set to Deliver
Custom Rules when set to deliver, bypass all filtering categories.
Verdict | Bypassed by Custom Rule? |
|---|---|
Spam | Yes |
Infomail | Yes |
Impersonation | Yes |
Malware | Yes |
Phishing | Yes |
Policy - Banned Attachment | Yes |
Policy - Geo Filter | Yes |
Create Custom Rule
Step 1: Click New
Navigate to the Policy page, click on Custom Rule, and then select New+.
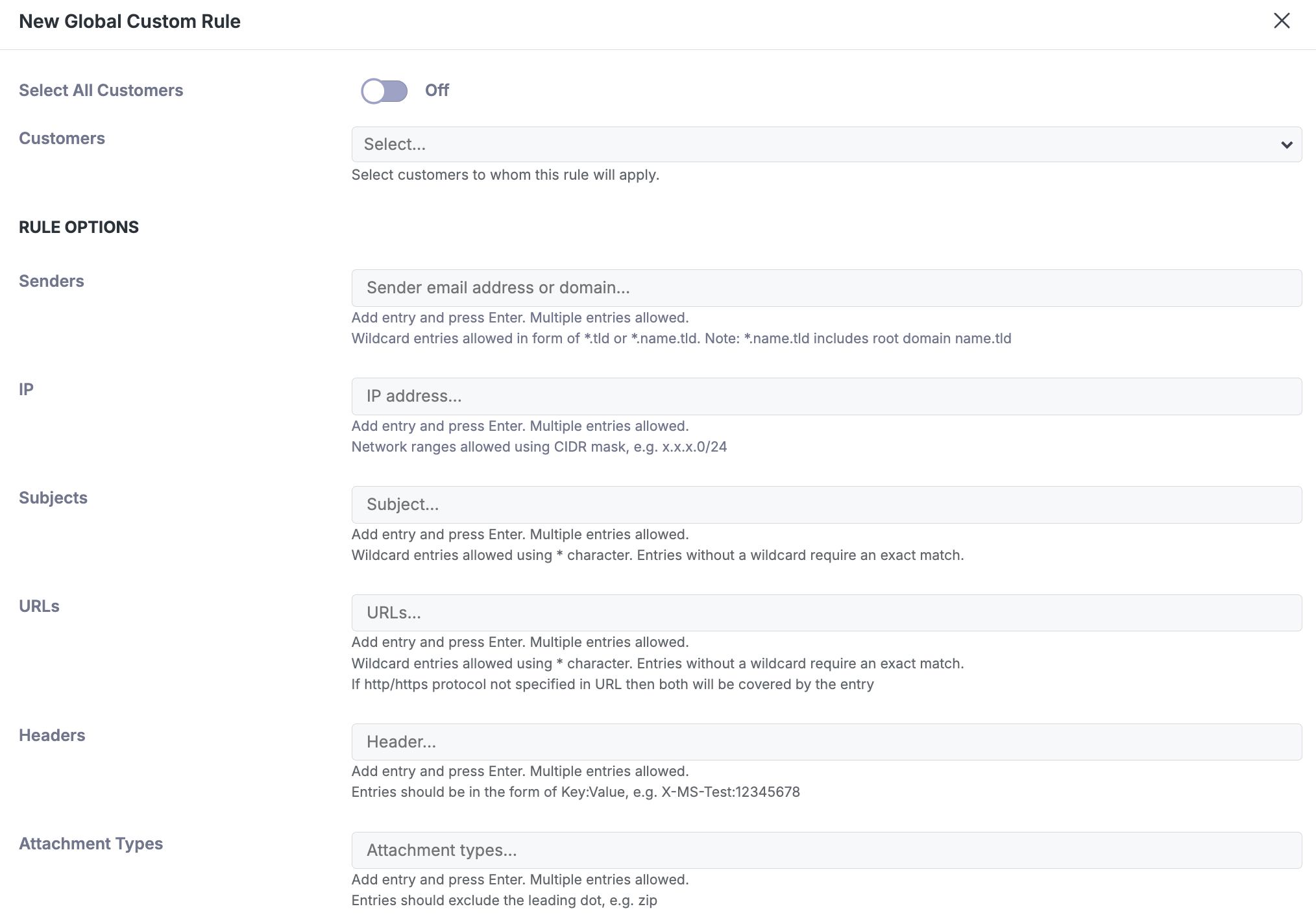
Step 2a: Select Customers to Whom the Rule Will Apply (Partner View)
When "Select All Customers" is enabled, the rule will select all existing customers or manually select the specific customers you want the rule to apply to.
Customers using different products may have different actions available to them.
Step 2b: Select Organization/Domain/User To Whom The Rule Will Apply (Customer view)
Select if you are applying the rule to the “Organization”, “Domain”, or a particular “User”.
Step 3: Select The Rule Options
For each section, one or more entries are allowed, and each section must have at least one match in the message for the rule to trigger.
Important: Each section in a custom rule functions as an AND statement, however, entries within an option function functions as an OR statement.
For example, a custom rule with one sender, one IP entry, two subject entries, and three attachments specified, the rule will require the message to contain at least one match from each entry to trigger the rule.
Sender
Rules will trigger if the header-from OR envelope-from matches the entry.
To allow a sender, enter the email address in this format: sender@example.com
To allow a domain AND all subdomains, enter the domain as shown below (do not include the '@' symbol): example.com
To allow a subdomain, enter the domain in this format (do not include the '@' symbol): subdomain.example.com
To create a wildcard entry, enter the rule in this format. This example would allow emails from domains ending in .io: *.io
IP
The sender's IP address or a pool of IP addresses, as shown below:
1.1.1.1
1.1.1.0/24
Subject
An exact match is required, unless using the wildcard symbol *.
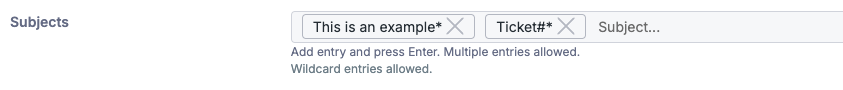
For example: The above rule will trigger on any subject lines starting with “This is an example" OR “Ticket#".
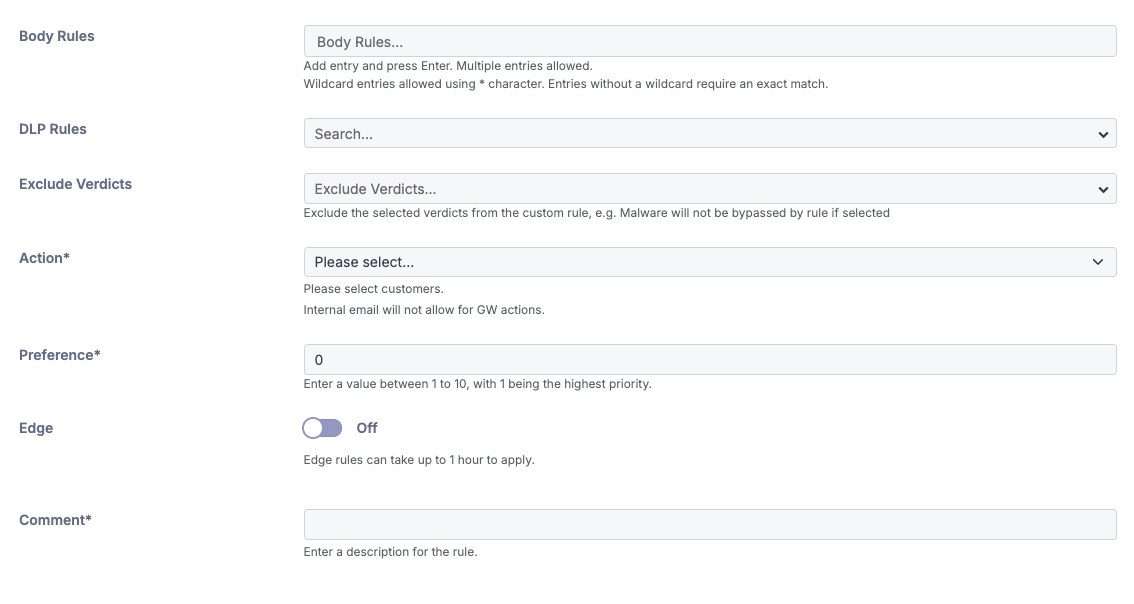
Body Rules
Define keywords/strings that, if found in the message body, will trigger the rule. It is possible to add one or more entries. Required to be a exact match unless using the wildcard symbol “*” which will allow for additional characters if inserted on the left, right or both sides of the entry. Each entry acts as a unique rule.
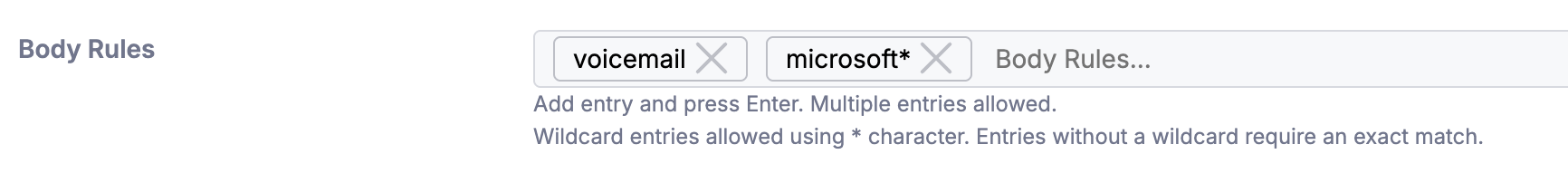
For example: The above rule will trigger on any emails containing the word “Voicemail" or lines starting with “Microsoft"
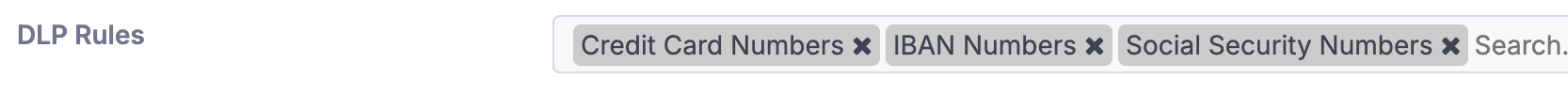
DLP (Data Loss Prevention) Rules
When enabled, DLP rules help identify and flag messages that contain patterns commonly associated with sensitive data. The current categories are Credit Card numbers, IBANs, or Social Security numbers (SSNs).
Credit Card Numbers
Matches industry-standard formats, e.g.5555-5555-5555-4444, 4111111111111111.IBANs
Matches valid IBAN formats (country-specific variations are supported).Social Security Numbers (SSNs)
Matches the standard U.S. SSN format (111-22-3333) as well as variations without separators (e.g.111223333).
Once a match is detected, the configured action for the rule (e.g. quarantine, reject, or banner the message) will be applied.
URL
Wildcard entries are allowed in the form of *.tld or *.name.tld. You can also use a wildcard at the end of a full address. If HTTP/HTTPS protocol is not specified in URL then both will be covered by the entry.
example.com
*.example.com
https://example.com/contact-us
https://example.com/*Headers
Used to identify specific email headers. This can help when allowing Security Awareness Tools or mass mailing services as they commonly will inject a unique custom header.
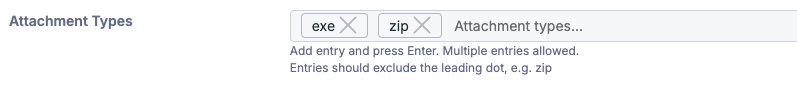
Attachment Type
Used to check for specific attachments. This can be used override the banned attachments specified in the customer’s policy or only trigger when. Entries should exclude the leading dot, e.g. zip.
Step 4: Exclude Verdicts
This option can be used to exclude a particular verdict in a custom allow rule.
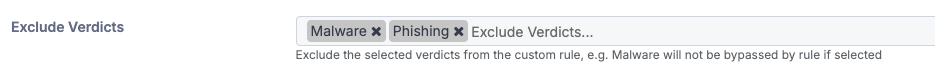
If this field is left empty, the custom rule will trigger for ALL verdicts. If you select an option from the dropdown menu, for example Malware or Impersonation, an email that receives either of those verdicts would not trigger the rule.
Step 5: Actions
Decide the action applied on the email.
Deliver
Deliver + Banner (Only available Mesh Unified and Mesh 365)
Delete
Quarantine
Reject
Junk (Only available Mesh Unified and Mesh 365)
Junk + Banner (Only available Mesh Unified and Mesh 365)
If an email has the Delete or Reject action it CANNOT be recovered.
Step 6: Preference
The preference controls when the rule is triggered if there are other custom rules you would like to process first. In most cases, 1 will be the most appropriate. Rules are still applied based on their hierarchy first. More info: Policy & Rule Hierarchy
Step 7: Edge Rule
The “Edge” slider should only be enabled if you wish to bypass SPF checks or DNS issues. Enabling this will carry out the action at the connection level. In most cases, you do not need to enable this.
Step 8: Comment
Text field to describe the rule and make searching in the future easier.
Step 9: Submit
Click Submit to save settings. The table will now be updated with the created rule.
